Start your journey with our Ethical Hacking Guide! Learn essential skills, tools, and certification paths to succeed in cybersecurity . During the period of global wars, terrorist groups hired hackers to penetrate computer networks, either to steal sensitive information or to demand large amounts of money with threats to lock down. This has resulted in increased cases of cybercrimes in the society. Companies are always under the pressure of updating their systems, applying multiple technologies to prevent possible hackers from penetrating their systems. “New worms”, “malware”, “viruses” and |ransomware| have emerged to cause havoc to the networks of business entities, government and defense departments, hence the increasing demand for ethical hacking services.
Currently, the government agencies and various companies require ethical hackers due to the rising threat in the field of IT security.
Specialists and companies have realized that guarding a system is not only about installing a set of security measures.
Complete Ethical Hacking Guide
What is Ethical Hacking?
Ethical hacking is the legal process of identifying security loopholes in an application, system or an organization’s infrastructure with the aim of simulating the possible breaches in a computer network. Ethical hackers seek to find vulnerabilities in systems or networks that the black hat hackers are capable of exploiting. They strive to enhance the security of these systems so as to combat or redirect threats.
In this particular case, ethical hackers are assigned certain roles and responsibilities that are mentioned below.
Roles and Responsibilities
To hack legally ethical hackers have to accept some rules. A proficient ethical hacker understands and follows these ethical guidelines, including…
Authorization
Ethical hackers can only do a security assessment on a system if they are authorized to do so by the owners of the system.
Scope Definition
They have to identify what aspects of the organization they are going to assess and explain their strategy to the management.
Reporting
Ethical hackers are supposed to report any loophole or any breach they find in the system or the network.
Confidentiality
They are forbidden to share their results and often sign non-disclosure agreements, as their main objective is to protect the system or network.
Cleanup
In this process, ethical hackers must clear all the signs that they have explored the vulnerability to avoid the same being exploited by other hackers.
Through the above guidelines, ethical hackers contribute greatly to the improvement of security in systems and networks and the safeguarding of information from attack.
Ethical hacking can be defined as the testing of an organization’s security measures by exploiting vulnerabilities to identify them to fix them.
Enhancing Corporate Security
The most important benefit of learning ethical hacking is its ability to enhance and secure companies. Since hackers are one of the most significant threats to any organization, the knowledge of their tactics will enable the network defenders to identify the risks of their organization and find ways of mitigating them. Furthermore, ethical hacking training or certification is useful for those who want to change to the security industry or those who want to prove their potential to their organization.
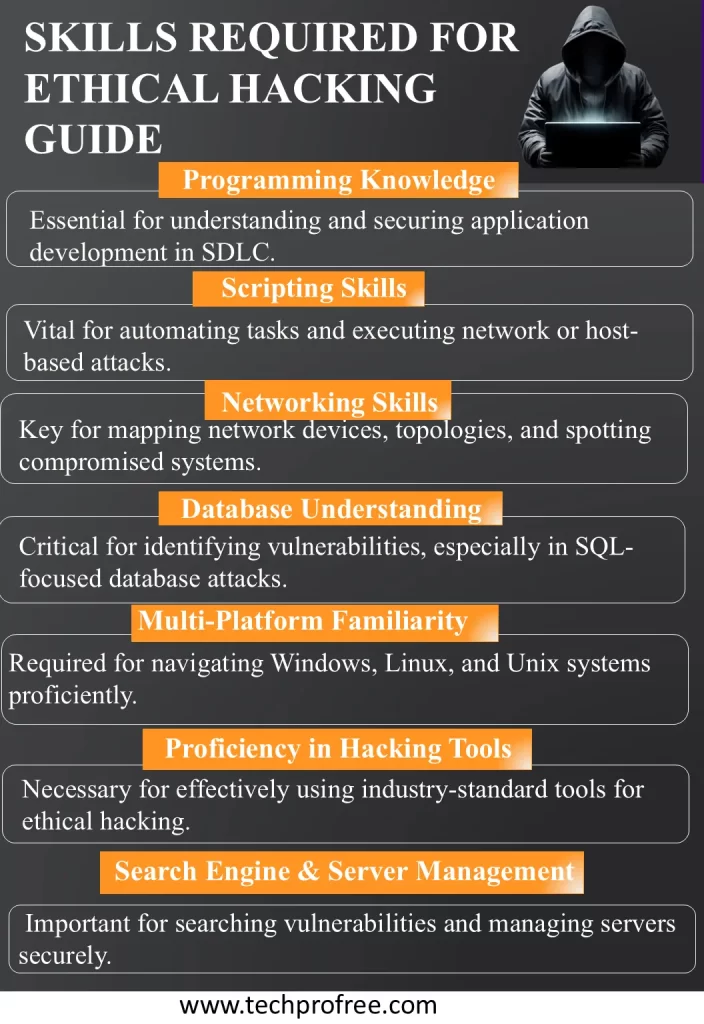
Skills Require To Become an Ethical Hacker
Ethical hacking entails a wide understanding of systems, networks, program codes and security features, thus making the ethical hacker position a very technical one. Key skills include:
Programming Knowledge
Recommended for anyone who is involved in any way in application security and/or the Software Development Life Cycle (SDLC). have grip on programming language
Scripting Knowledge
Especially for those who are struggling with network-based and host-based attacks.
Networking Skills
Essential when it comes to risk that stems from a network. This includes identifying all devices in a network, their topologies and being able to identify a compromised device.
Database Understanding
Since the attacks frequently focus on databases, understanding databases such as SQL is essential while examining the operations.
Familiarity with Multiple Platforms
Windows, Linux, and Unix operating systems with computer proficiency.
Proficiency with Hacking Tools
It is with the help of these that one is capable of using various hacking tools available in the market.
Search Engine and Server Knowledge
Knowing how to work with search engines and how to manage servers.
Final Words
Cybercrime has become on the rise; there is a need to fortify the strategies. Ethical hacking stands out as an essential tool, which seeks to use legal means to search for the weaknesses that the hackers are likely to exploit. This guide reviewed the questions of what ethical hacking is, why it is important, and how it is done while observing the ethical standards. Through active prevention and the enhancement of protection, ethical hacking protects information, builds confidence in the online world and creates the basis for a secure cyberspace era. If it is your first time to consider a career in IT or you are an already experienced one, ethical hacking is a fulfilling career as you become a protector of the new age technology.



Leave a Comment