As we approach 2025, it’s more important than ever for organizations to grasp the cybersecurity trends shaping our digital world. With cyber attacks becoming increasingly sophisticated, staying up to date on the latest practices and technologies in cybersecurity is vital for safeguarding businesses and protecting valuable data. Embracing these trends will help ensure that we can confidently navigate the evolving threat landscape . Due to the development of generative AI and the accelerated pace of digital transformation, organizations have had to deal with and oversee substantial shifts in their operations. For the leaders in security and risk management that are now in the phases of recovery and adaptation to the recent disruptions, there is a need to incorporate the strategic planning assumptions going forward into the resource investment decisions, product choices, and the prioritization of services and initiatives.
Therefore it is crucial to update oneself with the new trends in cybersecurity and employ measures that can prevent new threats from happening. New statistics show that 29% of the companies suffered severe consequences of a cyber-attack in the last year. To protect your organization from such increasing threats in 2025 and beyond, it is essential to know and adopt the future/current trends in cybersecurity.
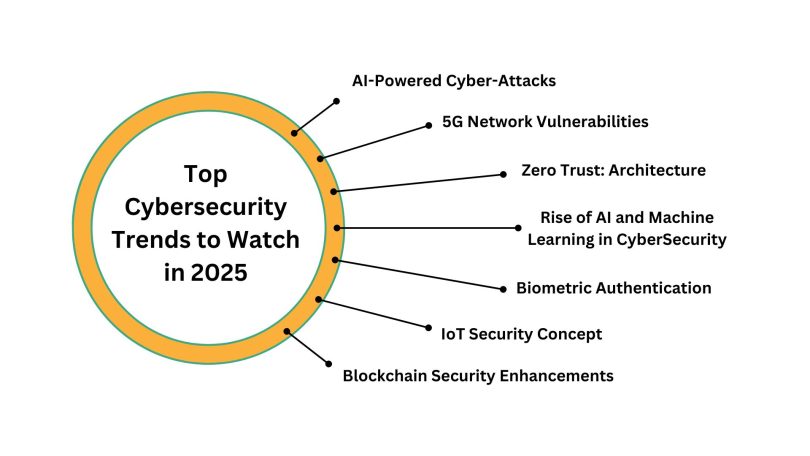
Top Significant Cybersecurity Trends /Issues for 2025
Cybersecurity in 2025 needs to be an integral part of your IT strategy because the threats are only getting more and more complex.
The following trends are expected to shape the evolution of cyber threats in the coming 2025:
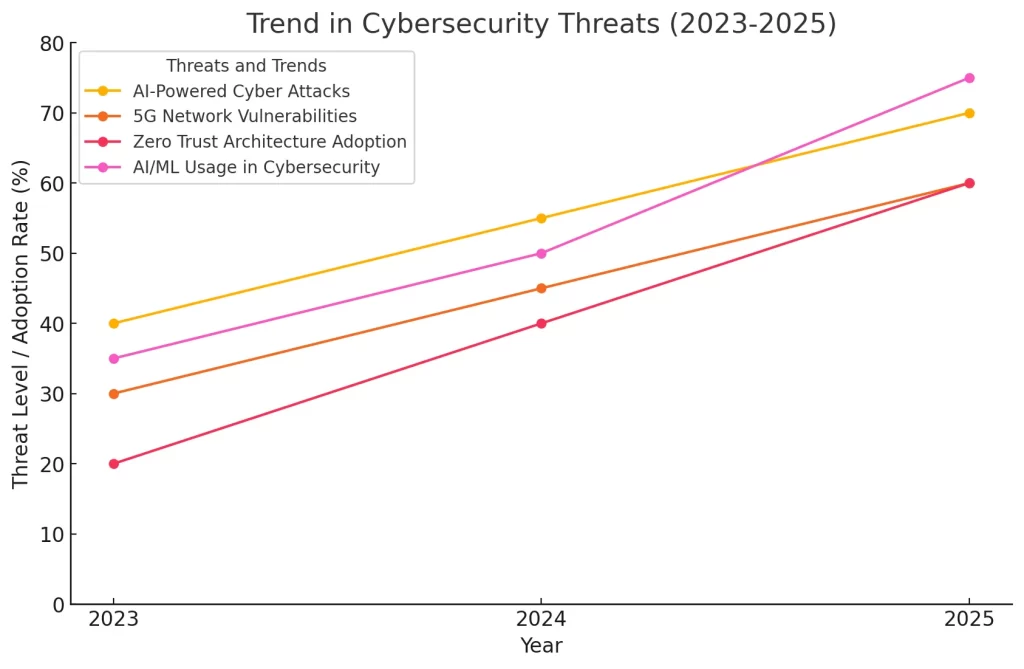
AI-Powered Cyber-Attacks
As the AI progresses, cyber attackers are employing these technologies to perform more elaborate and precise attacks. AI-based phishing attacks and the creation of malware using AI and AI-based social engineering techniques are some of the biggest threats to traditional security measures. So, stakeholders or establishments must strengthen their cybersecurity systems with AI-based threat identification and countermeasures to prevent new threats and the corresponding risks.
5G Network Vulnerabilities
The availability of the fifth generation of networks means fast and global connection, but it has its drawbacks in terms of protection. Various threats such as the network slicing attack and IoT devices put into question the security of 5G networks and require the establishment of proper security measures and models.
Zero Trust: Architecture
The Zero Trust model that works under the “never trust, always verify” model is expected to become the norm in cybersecurity. In 2025, the number of organizations that have integrated Zero Trust principles into the protection of networks and data will increase, making every request for access to be validated and validated before granting access.
Rise of AI and Machine Learning in CyberSecurity
AI and ML will be the key drivers for the future development of threat detection and response. These technologies will allow organizations to detect and counter threats as they happen, be more responsive to emerging threats and minimize the time of vulnerability to cyber criminals.
learn about Machine Learning Helps in Cyber Security In Detail
Due to the development of generative AI and the accelerated pace of digital transformation, organizations have had to deal with and oversee substantial shifts in their operations. For the leaders in security and risk management that are now in the phases of recovery and adaptation to the recent disruptions, there is a need to incorporate the strategic planning assumptions going forward into the resource investment decisions, product choices, and the prioritization of services and initiatives.
Therefore it is crucial to update oneself with the new trends in cybersecurity and employ measures that can prevent new threats from happening. New statistics show that 29% of the companies suffered severe consequences of a cyber-attack in the last year. To protect your organization from such increasing threats in 2025 and beyond, it is essential to know and adopt the future/current trends in cybersecurity.
Top Significant Cybersecurity Trends /Issues for 2025
Cybersecurity in 2025 needs to be an integral part of your IT strategy because the threats are only getting more and more complex.
The following trends are expected to shape the evolution of cyber threats in the coming 2025:
AI-Powered Cyber-Attacks
As the AI progresses, cyber attackers are employing these technologies to perform more elaborate and precise attacks. AI-based phishing attacks and the creation of malware using AI and AI-based social engineering techniques are some of the biggest threats to traditional security measures. So, stakeholders or establishments must strengthen their cybersecurity systems with AI-based threat identification and countermeasures to prevent new threats and the corresponding risks.
5G Network Vulnerabilities
The availability of the fifth generation of networks means fast and global connection, but it has its drawbacks in terms of protection. Various threats such as the network slicing attack and IoT devices put into question the security of 5G networks and require the establishment of proper security measures and models.
Zero Trust: Architecture
The Zero Trust model that works under the “never trust, always verify” model is expected to become the norm in cybersecurity. In 2025, the number of organizations that have integrated Zero Trust principles into the protection of networks and data will increase, making every request for access to be validated and validated before granting access.
Rise of AI and Machine Learning in CyberSecurity
AI and ML will be the key drivers for the future development of threat detection and response. These technologies will allow organizations to detect and counter threats as they happen, be more responsive to emerging threats and minimize the time of vulnerability to cyber criminals.